Prototype
Prototype
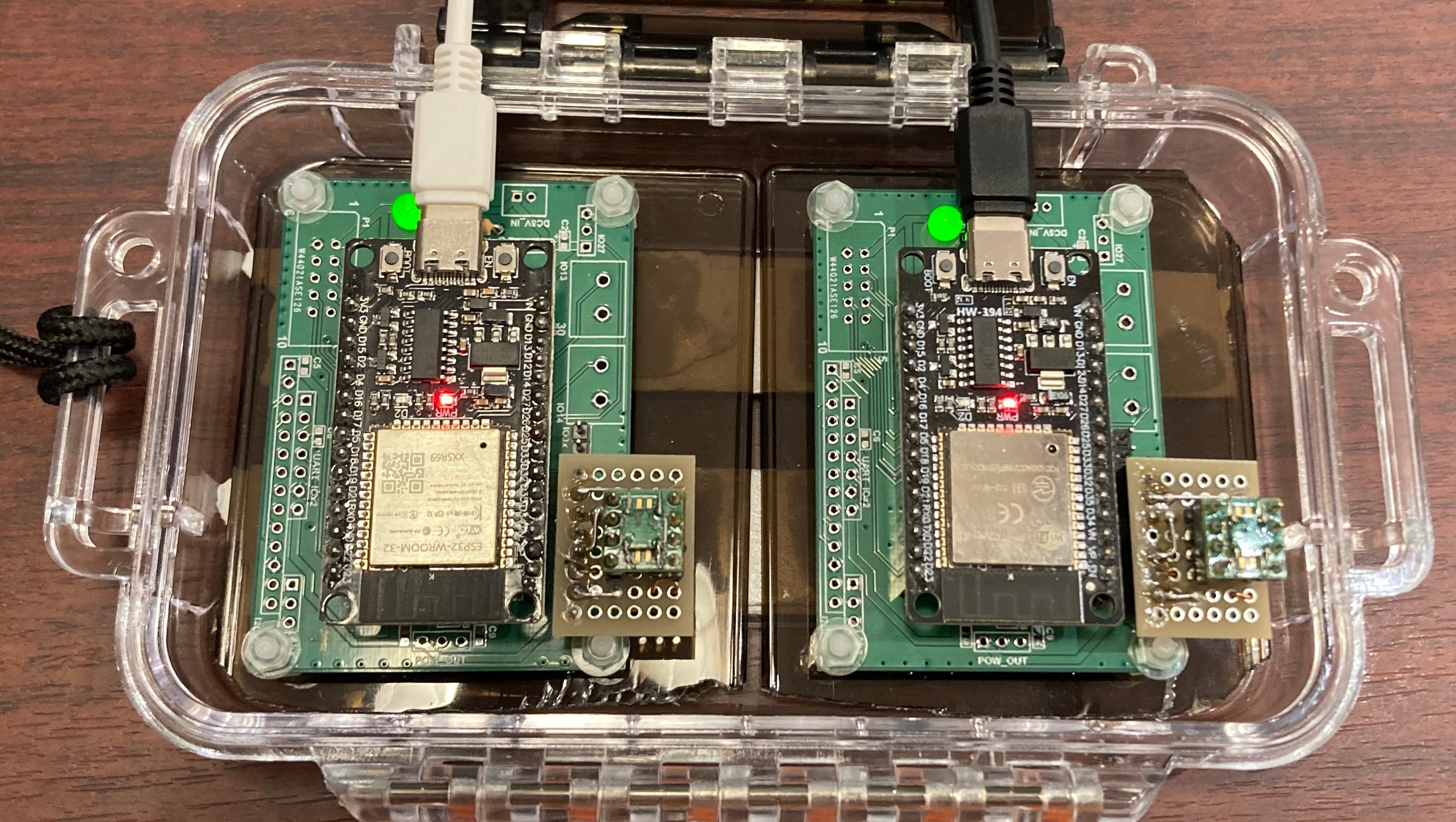
This is an actual quantum cryptographic device.
The left and right sides are separated into the host side and terminal side, and the structure allows you to check the connection status of both sides on the computer screen. *A developed quantum chip is mounted on the bottom right edge of each.
Connection screen
It has a simple structure that allows you to check the pairing status by displaying an easy-to-understand numerical representation of random numbers generated by random atomic decay sent from both quantum chips through the base.

The composition of the connected photo above represents the following conditions.


This prototype can be used to analyze the XOR of quantum cryptographic connected states. This makes it possible to confirm the safety of quantum chips. (Being able to analyze XOR = breaking quantum cryptography)
The world's first true random number generator using atomic decay
Previously, due to *parity violation, which was proven by Yang and Li, who won the Nobel Prize in Physics in 1956, it was believed that during the atomic decay process (α decay, β decay), the beta particles during β decay were not completely random. It had been proven that there was no such thing. Therefore, even alpha particles were not known to be completely random. *However, in 2022, Japanese researchers used parity symmetry to prove that the alpha particles emitted by atomic nuclei during alpha decay are completely random. This paper is published in the global science media Nature.

Base technology: Secure random number generation from parity symmetric radiations
Probability of true random numbers
Although researchers around the world are conducting research on true random numbers, there are only a few practical true random number generators, and most of them use photons. Our random number generator utilizes the unique principle of atomic decay, and the energy that generates random numbers is generated by the energy of natural decay, so it is a mechanism that can emit unlimited energy for 432 years. Therefore, it consumes much less energy than similar devices using photons and does not generate heat.
In the future, as the computing power of processors improves and more efficient algorithms are discovered, it is possible that current cryptographic methods will no longer be sufficient. Furthermore, in recent years, with the development of quantum computers, it is predicted that even complex codes with large numbers of digits can be broken in a short amount of time. It is said that most codes can be broken using the famous Shore algorithm.
By using truly random numbers like this, it is possible to prevent security threats and code breaking due to the spread of quantum computers.
Last updated